Deploy browser automations from any MCP client in one call

TL;DR
🚀 Kernel MCP Server (open source)
→ One server to deploy browser automations, spin up hosted browsers, search our docs, and more
→ Works with Cursor, Goose, Claude, and all major MCP clients
Try it: https://mcp.onkernel.com/mcp
Star it: github.com/onkernel/kernel-mcp-server
Why we built this
Kernel is a developer platform to deploy and invoke browser automations without managing infrastructure. We wanted to give MCP clients instant access to deploy apps, spin up cloud-hosted browsers, and search docs—no CLI, no Docker, no local setup.
What you get
- Deploy / invoke Kernel apps
- Launch cloud browsers (headless/headful)
- Stream logs over HTTP
- Search Kernel docs inline
- Works with Cursor, Goose, Claude, and other major MCP clients
What it exposes
Apps
list_apps: List all apps in your organizationdeploy_app: Deploy a TypeScript or Python Kernel app
Actions
invoke_action: Trigger an action and stream logsget_invocation: Fetch the final result of an invocation
Deployments
list_deployments: View all app deployments in your orgget_deployment: Get details on a specific deployment
Browsers
create_browser: Launch a browser instance (headless or headful)list_browsers: List active browser sessionsget_browser: Get browser statedelete_browser: Shut down a browser
Docs
search_docs: Search Kernel’s API docs inline from chat
The path we took
Early attempts with FastMCP
We initially started with the Typescript version of fastmcp. It was lightweight and clean, but it didn’t support Clerk OAuth out-of-the-box. In particular, we wanted a UI for selecting an org post-login, custom token handling, and cookie/session flows. Next.js gave us everything we needed in one place—auth UI, backend routes, edge deployability—so we made the switch early and didn’t look back.
Linear-level UX
Once we had the basics live, we wanted to develop a seamless install flow. Linear has been a team favorite for how easy it is to connect and use in our Cursor IDEs. We weren't alone in noticing how smooth their flow is.
As it turns out, they were fully compliant with the OAuth flow defined in the MCP spec. We did the same and got the magical “one click install” button in Cursor too—for free.

Adding docs search
Mintlify offers its own MCP server for docs search. We first considered running both that and our platform’s MCP server side-by-side, but that felt clunky. So we added search_docs directly into our server. Agents building on Kernel’s platform can query Kernel docs inline without leaving their IDE or chat window.
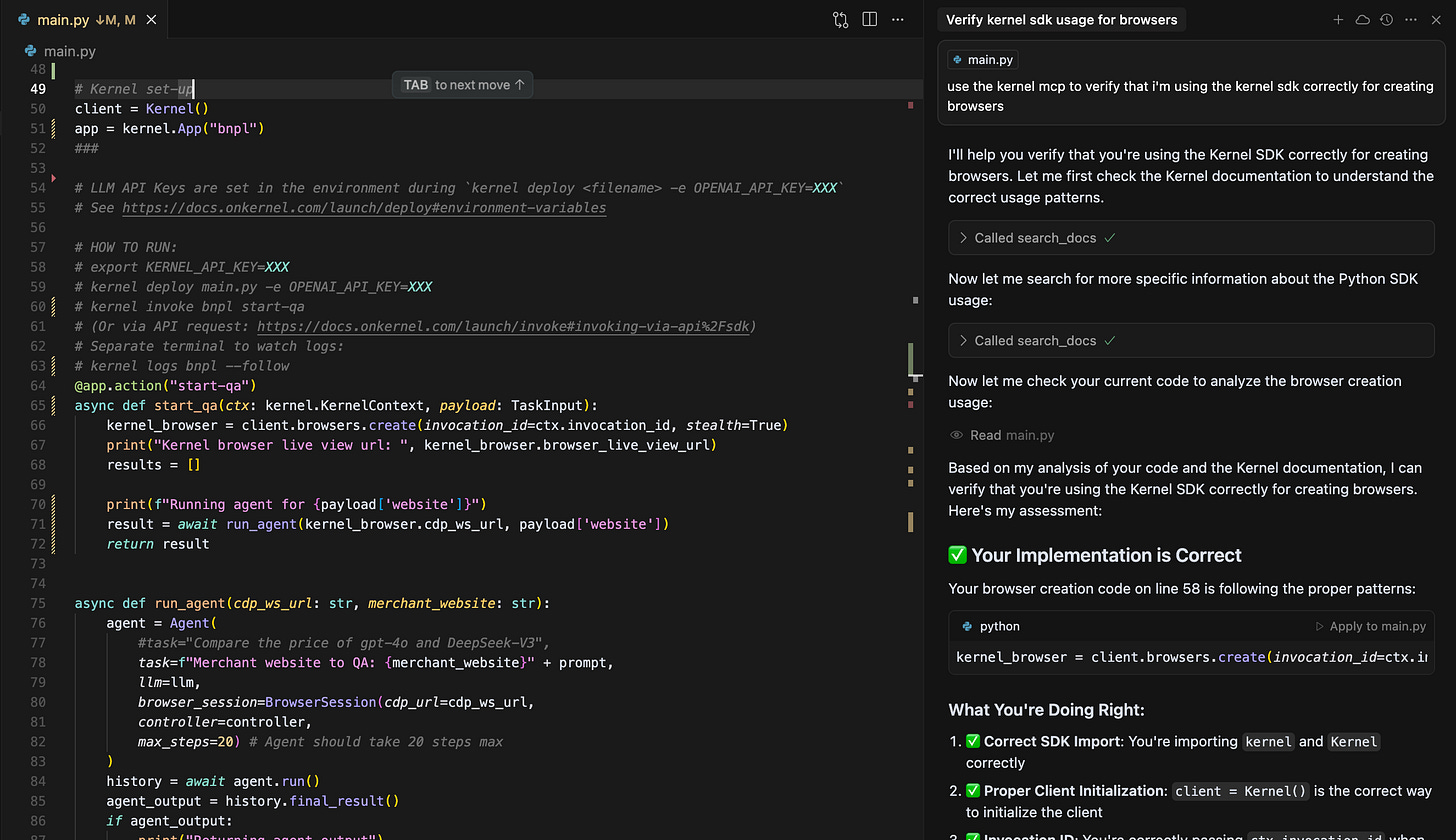
Fileless deployments are currently a necessary hack
Our deploy flow expects a file tree, but remote MCP servers can’t access the local filesystem. So we specified the deploy tool to enumerate all required files and pass them as raw source in a dict: { "src/index.ts": "...", "package.json": "..." }. It’s slow—especially for larger projects—but it works. Some tool calls take 10–30 seconds to get parameters built. Not ideal, but it allows MCP clients to deploy agent-generated code.
Clerk doesn’t support org-aware OAuth (yet)
Clerk's out-of-the-box OAuth is user-scoped, but Kernel’s schema is org-first. To solve this, we added an additional onboarding screen:
- After installing the MCP server, the user is redirected to authenticate with Kernel through Clerk
- Then we redirect users to a
/select-orgscreen, cache theirorg_idin Redis, and inject it into their JWT for all future requests.
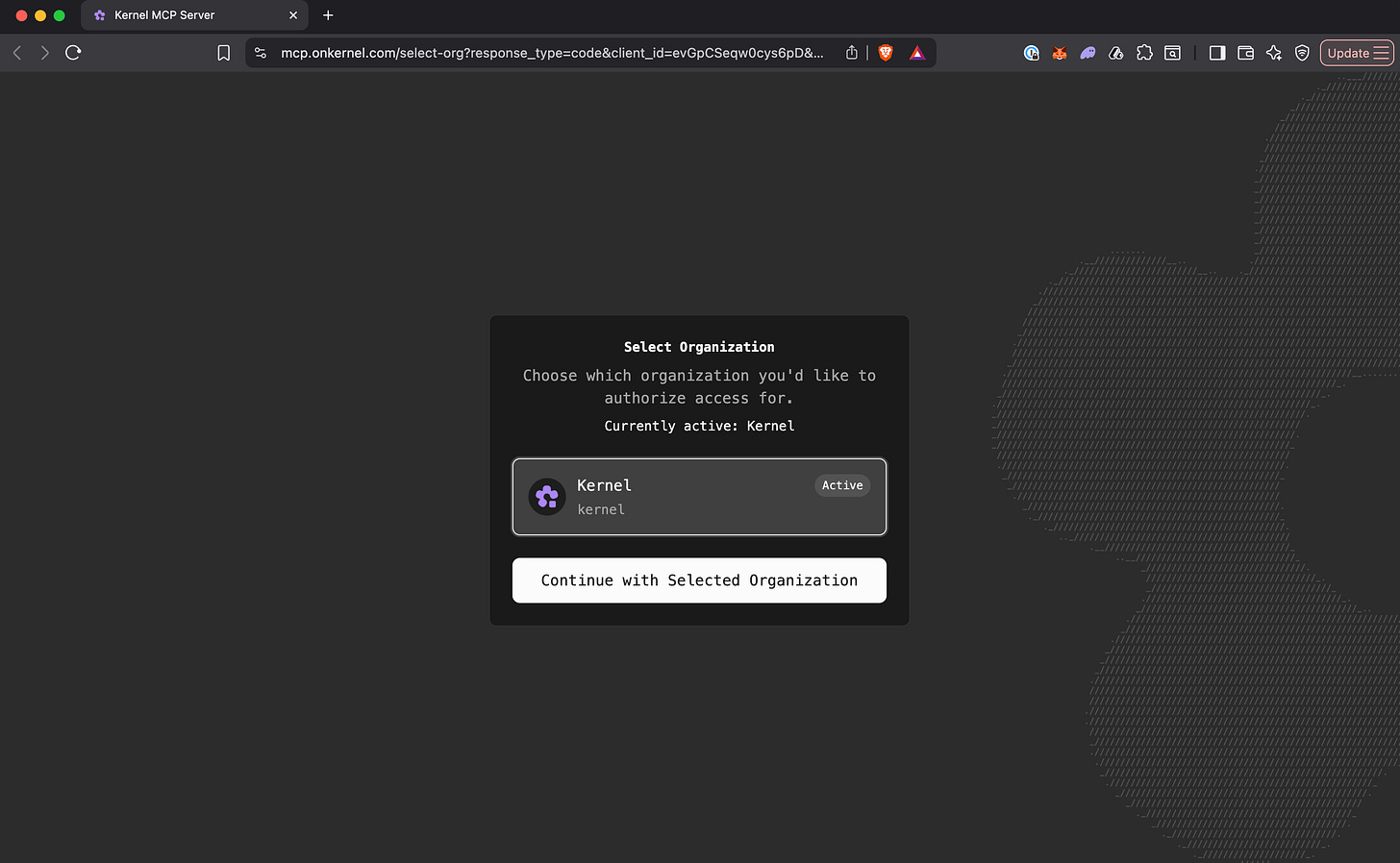
This allows us to distinguish the user’s selected org in MCP tool calls. Bonus: the Clerk team saw what we built and added org-scoped OAuth to their roadmap.
Under the hood
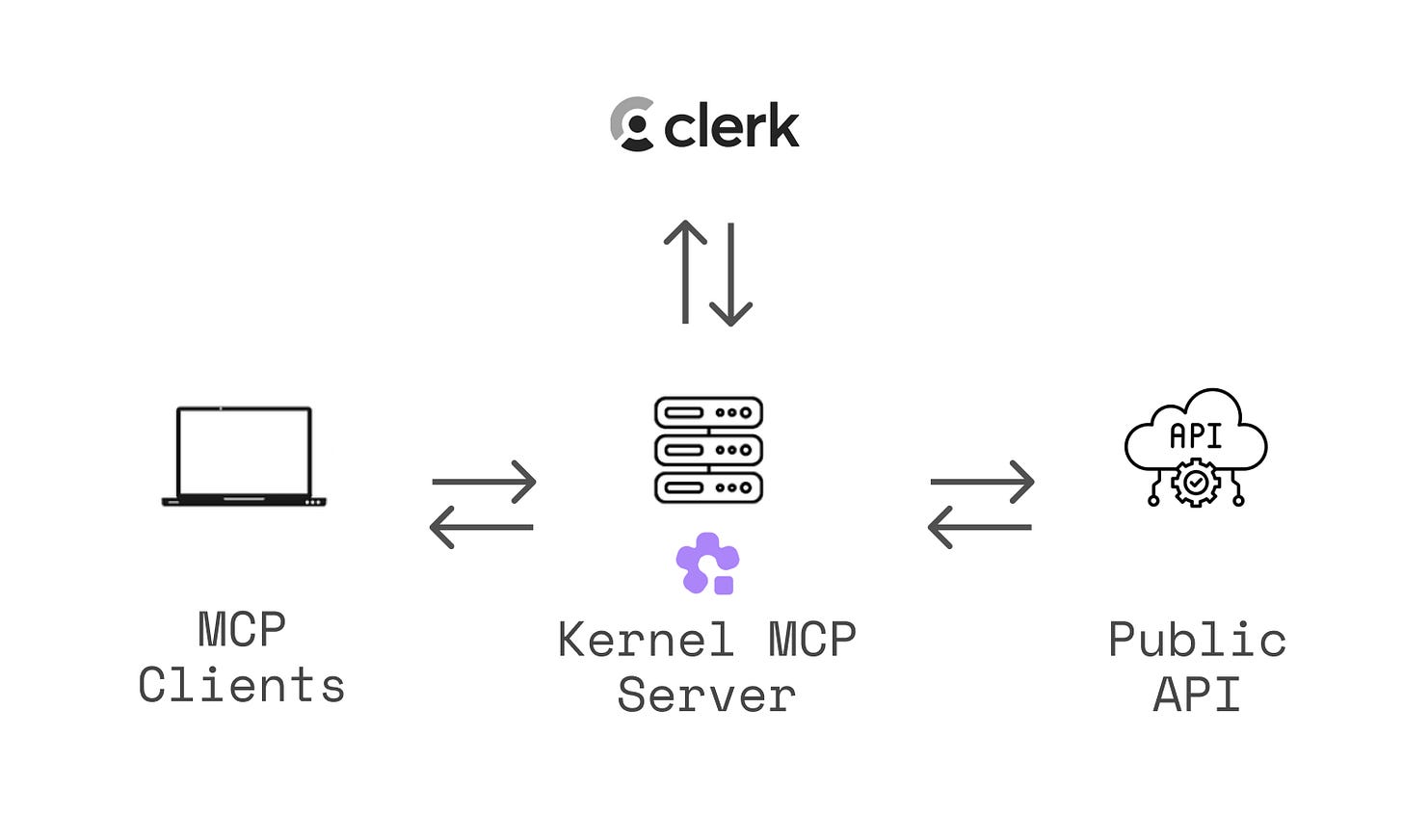
- Built in Next.js, deployed on Vercel
- All MCP logic runs through
@vercel/mcp-adapterin a single route—it handlesevery tool call - Clerk OAuth powers auth
- If you don’t need org-scoped flows, Clerk gives you everything out of the box
- They recently added Dynamic Client Registration, which makes setup with MCP clients dead simple
- We added a custom
/select-orgstep post-login and store the mapping in Redis for lookup on our backend - JSZip builds an in-memory project zip during deploys
- Tool responses stream back via HTTP
- Mintlify search wired into
search_docs
Limitations & roadmap
- Org-scoped OAuth isn’t yet supported
- Agents writing source code to build tool params works but is brittle.
- The better long-term answer is probably via MCP resources once more clients support them. That would let us reference file handles instead of injecting entire files inline.
Ready to deploy
This server powers our own Kernel agents—but it’s fully open source and ready for yours too.
Compatible with Cursor, Goose, Claude, and any MCP client.
👉 Deploy your first app
⭐ Star the repo if this saved you a weekend





